- INFORMATION TECHNOLOGY (IT) & ARTIFICIAL INTELLIGENCE (AI)
- ARTIFICIAL INTELLIGENCE.
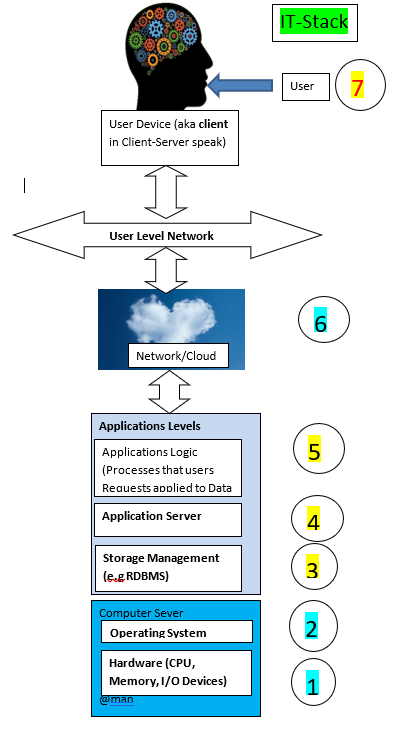
- The 7L IT curriculum is derived from the IT-Stack (below) Framework. At the end-of each layer, in the 7L, exams and International Standardized certification tests can be setup, if request by the customer. The idea is to form Layer based experts, like O.S/RDBMS/Applications/Network System Administrators and Support Engineers, or Developers and Managers having an overall view of the Stack. Thus the Specializations can be based on one or more layers of the IT-Stack. As an Example, an Ecommerce Application (EC) Software Engineer need to understand layers 2-to-6 even if they develop code just around the Web-Server (Application Server) environment. That’s because EC Application need to interact over the Network/Cloud (from the top) and the RDBMS and O.S from the bottom. Thus understanding the Security and performance requirements are prerequisites to writing great EC Applications.
- Artif
- The 7L IT curriculum is derived from the IT-Stack (below) Framework. At the end-of each layer, in the 7L, exams and International Standardized certification tests can be setup, if request by the customer. The idea is to form Layer based experts, like O.S/RDBMS/Applications/Network System Administrators and Support Engineers, or Developers and Managers having an overall view of the Stack. Thus the Specializations can be based on one or more layers of the IT-Stack. As an Example, an Ecommerce Application (EC) Software Engineer need to understand layers 2-to-6 even if they develop code just around the Web-Server (Application Server) environment. That’s because EC Application need to interact over the Network/Cloud (from the top) and the RDBMS and O.S from the bottom. Thus understanding the Security and performance requirements are prerequisites to writing great EC Applications.
- STEM
- Our STEM philosophy is that everything is connected! Thus studying Math needs to reference where and why it’s needed in Physics, or IT, or Chemistry.
- The other dimension we consider is the presentation of the studied topics from different, or combined, Human Senses angles. Our belief is that one may not comprehend a Concept, C, just through cognition (Brain-use only/Thought). Some times the explanation needs to be extended through other senses like visual, auditory, olfactive, experimentation (touch, taste).
- IT SECURITY
- Our Approach to IT-Security uses the IT-Stack (see below) as a starting point. We then identify the general security requirements and the IT-Stack Component specific Security. Likewise for the Vulnerabilities and Threats (V&T) we study the general, It-Stack wide and the Component Specific levels of V&T.
- The Advanced Security topics are approached independently of the IT-Stack. Concepts and techniques studied along the IT-Stack security are only re-studied with audiences that didn’t go through all the IT Security curriculum.
- INVENTONOMICS
- Our methodologies for approaching Inventions and problem solving are ready. We, however, perfect them based on the audience level. For instance, our approach is to identify and illustrate problems in the equivalence class of the Audience and we apply to them Inventonomics techniques.
- IT and IT-Security based framework.
We provide consulting across a range of practices in IT, SAP, IT Security, STEM, Inventonomics and more. Our consulting can be applied in may ways.
- Identifying knowledge and knowhow gaps and developing or recommending courseware, and related tools and experiments that help the learners close knowledge gaps or develop additional expertise.
- Hands-on deployment of IT-Stack Components along with knowledge transfer. Functions like Security audits, or tools deployments, SAP Systems & Applications Installation, Configuration, and Administration.